Table of Contents
HIPAA compliance is far from a new concept in the healthcare industry. I’m sure you have probably heard of it a couple of times or even several times in your healthcare industry. HIPAA stands for the Health Insurance Portability and Accountability Act, which was passed in 1996. The act was designed to protect the privacy and security of patients’ personal health information (PHI).
What is HIPAA Compliance?
HIPAA compliance is a set of regulatory standards that outline the lawful use and disclosure of PHI by covered entities and business associates.
Covered entities include healthcare providers, health plans, and healthcare clearinghouses. Meanwhile, business associates are individuals or organizations that perform functions or services on behalf of covered entities and require access to PHI.

Failure to comply with HIPAA regulations can result in significant financial penalties and damage an organization’s reputation. Therefore, covered entities and business associates need to understand the rules and requirements of HIPAA compliance to protect patients’ PHI and avoid costly violations.
Understanding HIPAA
HIPAA is a federal law that sets standards for protecting sensitive patient health information from being disclosed without the patient’s consent or knowledge. HIPAA applies to healthcare providers, health plans, and healthcare clearinghouses, as well as their business associates with access to patient information.
History of HIPAA
HIPAA was signed into law in 1996 by President Bill Clinton. The law was enacted to improve the efficiency and effectiveness of the healthcare system by standardizing electronic healthcare transactions, protecting the privacy and security of patient health information, and ensuring the portability of health insurance coverage for workers who change jobs.
Key HIPAA Regulations
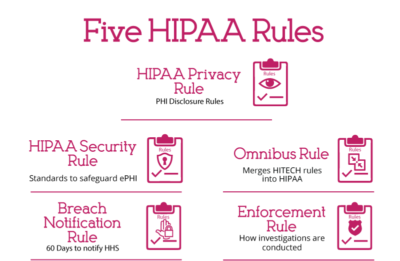
HIPAA consists of several regulations that healthcare providers, health plans, and other covered entities must comply with to protect patient health information. Some of the key HIPAA regulations include:
- Privacy Rule: This regulation sets national standards for protecting the privacy of individually identifiable health information.
- Security Rule: This regulation establishes national standards for protecting electronic personal health information (ePHI) created, received, used, or maintained by a covered entity.
- Breach Notification Rule: This regulation requires covered entities to notify affected individuals, the Secretary of Health and Human Services, and, in some cases, the media in the event of a breach of unsecured protected health information (PHI).
- Omnibus Rule: This regulation significantly changed the HIPAA Privacy, Security, and Enforcement Rules and the Breach Notification Rule.
- Enforcement Rule: This rule states how investigations should be carried out in the case of HIPAA violation.
Protected Health Information (PHI)

PHI is any information that can be used to identify an individual and relates to their past, present, or future physical or mental health condition, the provision of healthcare, or payment for healthcare services. Some examples of PHI include:
- Name
- Address
- Social Security number
- Medical record number
- Prescription information
- Diagnosis information
Tips to Stay Compliant

To stay compliant with HIPAA regulations, covered entities should:
- Develop and implement policies and procedures that comply with HIPAA regulations.HIPAA requires you to have written policies and procedures that address the use, storage, and disclosure of ePHI. Your policies and procedures must cover several areas, including access controls, data backup and recovery, device and media controls, and workforce security. You must regularly review and update your policies and procedures to ensure that they remain current and effective.
- Train employees on HIPAA regulations and the importance of protecting patient health information. Your employees are one of the most significant risks to the security of ePHI. HIPAA requires you to provide regular training to your employees on the policies and procedures related to using, storing, and disclosing ePHI. You must also ensure that your employees understand the risks associated with ePHI and how to identify and report potential security incidents.
- If you work with third-party vendors who handle ePHI on your behalf, you must have a business associate agreement (BAA) in place. A BAA is a legal agreement that outlines the responsibilities and obligations of both parties regarding ePHI. You must ensure that your BAAs are current and that your vendors are HIPAA compliant.
- HIPAA requires you to have an incident response plan that outlines the steps you will take in case of a security incident involving ePHI. You must also have a process for reporting security incidents to the appropriate authorities, including affected individuals and the Department of Health and Human Services. Regularly testing and updating your incident response plan is essential to ensure that it remains effective.
- Conduct regular risk assessments to identify potential vulnerabilities and implement appropriate safeguards.
- Limit access to patient health information to only those employees who need it to perform their job duties.
- Ensure that business associates with access to patient health information also comply with HIPAA regulations.
HIPAA Compliance Requirements

You must implement administrative, physical, and technical safeguards to ensure that your organisation complies with HIPAA regulations. These safeguards are designed to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI).
Administrative Safeguards
Administrative safeguards are policies and procedures that your organization must implement to manage the conduct of your workforce in relation to ePHI. Some of the administrative safeguards that you need to implement are:
- Security Management Process: Develop and implement policies and procedures to prevent, detect, contain, and correct security violations.
- Assigned Security Responsibility: Designate a security official who is responsible for developing and implementing security policies and procedures.
- Workforce Security: Implement policies and procedures to ensure that your workforce has appropriate access to ePHI based on their job roles.
- Security Awareness and Training: Provide security awareness and training to your workforce to ensure that they are aware of the security risks associated with ePHI and know how to protect it.
- Security Incident Procedures: Develop and implement policies and procedures to identify and respond to security incidents.
Physical Safeguards
Physical safeguards are physical measures that your organization must implement to protect ePHI from unauthorized access, theft, or damage. Some of the physical safeguards that you need to implement are:
- Facility Access Controls: Implement policies and procedures to limit physical access to your facilities where ePHI is stored.
- Workstation Use: Implement policies and procedures to specify the proper use of workstations that access ePHI.
- Workstation Security: Implement physical safeguards to protect workstations that access ePHI from unauthorized access, theft, or damage.
- Device and Media Controls: Implement policies and procedures to ensure that ePHI is removed from electronic media before it is reused or disposed of.
Technical Safeguards
Technical safeguards are technical measures that your organization must implement to protect ePHI from unauthorized access, theft, or damage. Some of the technical safeguards that you need to implement are:
- Access Control: Implement technical policies and procedures to limit access to ePHI based on the job roles of your workforce.
- Audit Controls: Implement technical policies and procedures to record and examine activity in systems that contain or use ePHI.
- Integrity Controls: Implement technical policies and procedures to ensure that ePHI is not improperly altered or destroyed.
- Transmission Security: Implement technical policies and procedures to protect ePHI from unauthorized access during transmission.
Risk Assessment and Management

HIPAA requires covered entities and business associates to conduct a risk assessment to identify threats to the confidentiality, integrity, and availability of electronic protected health information (ePHI).
A risk assessment is a systematic process that involves identifying and analyzing potential risks, evaluating the likelihood and impact of those risks, and implementing measures to mitigate or eliminate them.
Conducting a Risk Analysis
Conducting a risk analysis is the first step in identifying and implementing safeguards that comply with the HIPAA Security Rule. The Office for Civil Rights (OCR) recommends a four-step approach to conducting a risk analysis:
- Identify ePHI: Identify all ePHI that your organization creates, receives, maintains, or transmits.
- Identify Threats and Vulnerabilities: Identify all threats and vulnerabilities that could result in the unauthorized access, use, disclosure, modification, or destruction of ePHI.
- Assess Current Security Measures: Assess the effectiveness of your current security measures in place to safeguard ePHI.
- Determine the Likelihood and Impact of Threat Occurrence: Determine the likelihood and impact of each identified threat and vulnerability occurring.
Implementing a Risk Management Policy

After conducting a risk analysis, covered entities and business associates must implement a risk management policy to address the identified risks. A risk management policy is a set of policies, procedures, and controls that are put in place to mitigate or eliminate identified risks.
A risk management policy should include the following:
- Risk Mitigation Strategies: Identify and implement appropriate risk mitigation strategies to address identified risks.
- Risk Management Plan: Develop a risk management plan with a timeline for implementing risk mitigation strategies. The plan should also include ongoing monitoring and evaluation of the effectiveness of the risk management policy.
- Employee Training: Train all employees on the risk management policy and their role in safeguarding ePHI.
- Periodic Review: Conduct periodic reviews of the risk management policy to ensure that it remains up-to-date and effective.
Conducting a risk analysis and implementing a risk management policy ensures that covered entities and business associates comply with the HIPAA Security Rule. It also helps protect ePHI from unauthorized access, use, disclosure, modification, or destruction.
In conclusion, HIPAA compliance is paramount in healthcare to safeguard patients’ personal health information (PHI) and uphold their privacy rights.
Failure to adhere to HIPAA compliance regulations can result in severe penalties and reputational damage. Therefore, healthcare providers, health plans, clearinghouses, and their associates must understand and comply fully with these rules.
The key components of HIPAA compliance include maintaining administrative, physical, and technical safeguards to protect electronic PHI (ePHI), conducting regular risk assessments, implementing appropriate security measures, and providing comprehensive employee training.
When your organization adheres to HIPAA regulations, it ensures legal compliance and also demonstrates its commitment to protecting patients’ confidentiality, integrity, and availability of their health information.
To conclude, continual evaluation, training, and adaptation are essential to maintaining HIPAA compliance in an ever-evolving healthcare landscape, ultimately fostering trust between patients and healthcare providers while safeguarding sensitive health data.







